To begin, Birger saw the OSMC 2011 kick off, with an opening speech by Bernd where our new performance grapher, InGraph was also introduced. He then went off to Christoph Siess’ presentation, which gave a “Performance Comparison of Nagios Monitoring Solutions” (read Nagios, Icinga, Shinken, mod_gearman, Merlin). In short, he noted latency dramatically increases in Nagios 3.2.1 once a certain number of checks is exceeded. Nagios with mod_gearman and Shinken perform significantly better, while latency in Nagios, Icinga and Merlin were similar.
Ronny followed with a tool for statistical analysis of DNS servers. The DSC (DNS Statistics Collector) runs a collector on the server to record traffic flows in the form of a XML file every 60 seconds. This file is then converted by a presenter component for display in a CGI web interface. More information is available on the developer’s homepage.
Bernd then offered his impressions of the second OSMC day. After a big night atop the Nuremberg Christmas Market, almost all attendees made it to the conference rooms for two tracks of presentations on Nagios, Icinga with their related plugins and addons.
In between, Carsten offered an alternative to NSClient++ for windows monitoring – check_wmi_plus. As a plugin, check_wmi_plus offers agentless monitoring of a similar standard, implementing checks with performance data too. He noted that installation requires the WMI client for Linux, and gave some tips for configuring users and service monitoring in the command line with SubInACL. Documentation with more on useful checks is also within reach.
Also, Johannes shared a Python module for Windows Vista’s UAC, which he ported based on a suggested solution made by Aaron Margosis in his blog. Humbler.py resolves a problem similar to the LUA bug, where the user settings are at odds with the registered user.
Finally Pamela bid the OSMC 2011 farewell, thanking all participants, supporters and the Holiday Inn hotel for their contributions to a great event. She shared Jens-Christopf Brendel’s review in Admin Magazin and has since been busy filling the attendee area of the OSMC website with photos and presentation slides from the conference. The date for the next OSMC has been set for 17 – 18 October 2012, but before then, we hope to see you at our next event – the Open Source Data Center Conference on 25 – 26 April!
NETWAYS Blog
Windows-Monitoring mit check_wmi_plus
Heute stelle ich eine Alternative zu NSClient++ vor: check_wmi_plus.
check_wmi_plus erlaubt agentloses (d.h. es ist kein seperater Dienst auf dem Windows-Server zu installieren) Monitoring von Windows-Maschinen bei (fast) gleicher Standard-Funktionalität wie NSClient++, die jeweiligen Checks wurden auch inklusive Performance-Daten implementiert.
Dabei sind allerdings einige Fallstricke zu beachten, die ich hier erläutern werde.
Das Checkplugin selbst ist nach Installationsanleitung zu installieren, der WMI-Client für Linux (wmic) ist entweder aus Distributionspaketen zu installieren oder aus dem Quelltext, falls kein Paket vorliegt (z.B. Debian).
Anschließend ist auf dem zu überwachenden Windows-Server ein Benutzer anzulegen und wie folgt Rechte zu setzen:
- benötigte Windows-Gruppen: Distributed Com-Benutzer, Ereignisprotokolleser, Leistungsprotokollbenutzer, Leistungsüberwachungsbenutzer
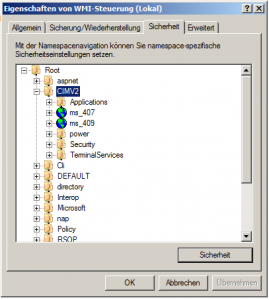
- im MMC-Snapin WMI-Steuerung dem Benutzer die Rechte Methoden ausführen, Konto aktivieren und Remoteaktivierung auf den Teilbaum ROOT\CIMV2 setzen:
Zum Überwachen von Services sind noch 2 weitere Schritte im Windows-CLI (cmd.exe) notwendig:
- Generelle Rechte für das Abfragen von Services für Remote freigeben:
sc sdset SCMANAGER D:(A;;CCLCRPRC;;;AU)(A;;CCLCRPRC;;;IU)(A;;CCLCRPRC;;;SU)(A;;CCLCRPWPRC;;;SY)(A;;KA;;;BA)S:(AU;FA;KA;;;WD)(AU;OIIOFA;GA;;;WD) - mittels SubInACL Rechte auf Services freigeben:
subinacl /service \\server\* /grant=domain\user=QSI
Abschließend ist noch zu Überprüfen ob der WMI-Dienst gestartet ist und ob die Windows-Firewall eventuell den WMI-Dienst blockiert.
Die nun nutzbaren Checks sind hier dokumentiert.